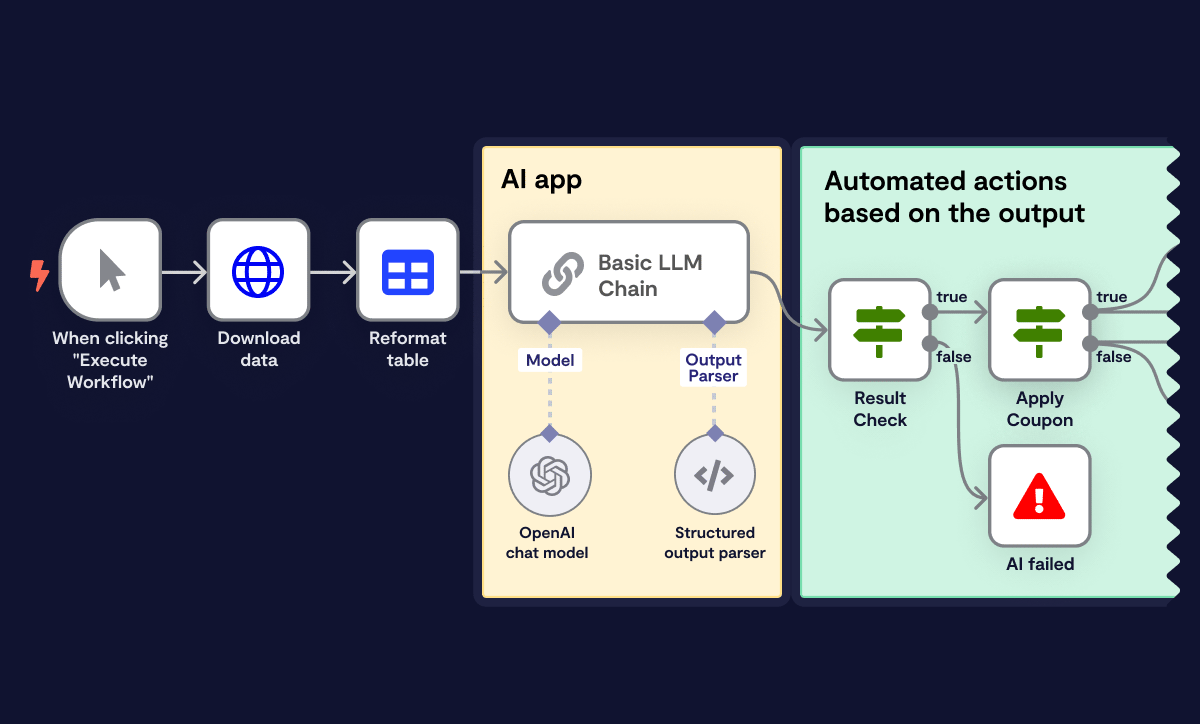
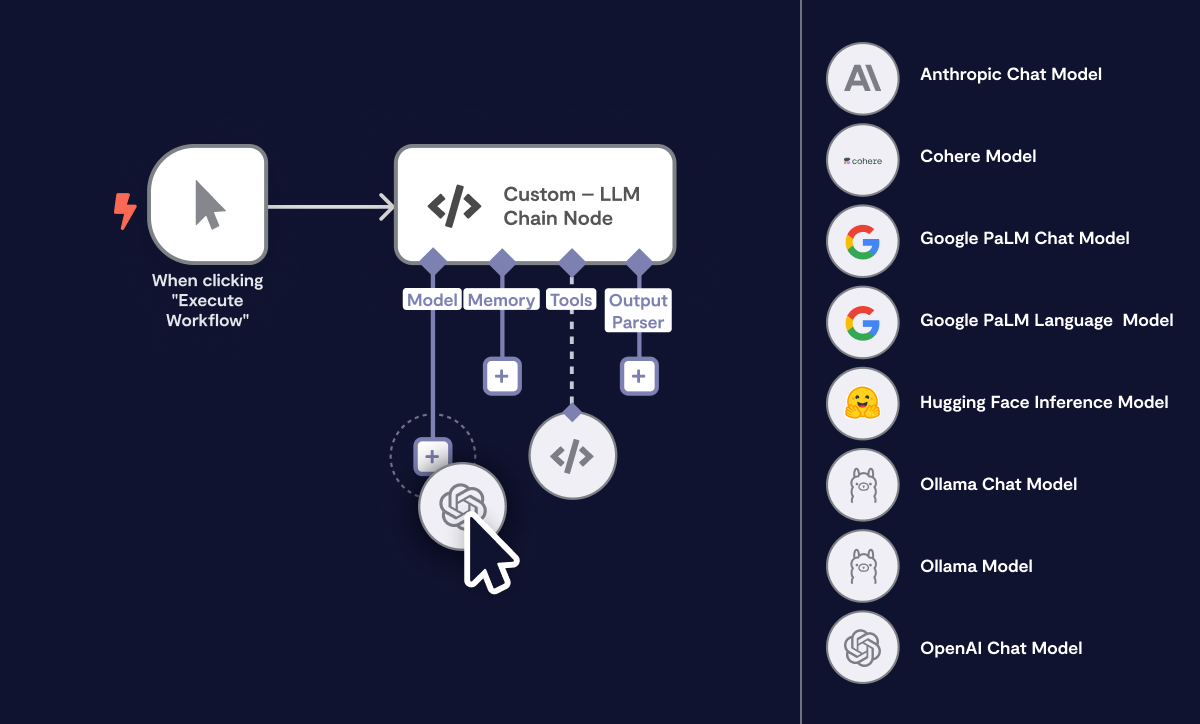
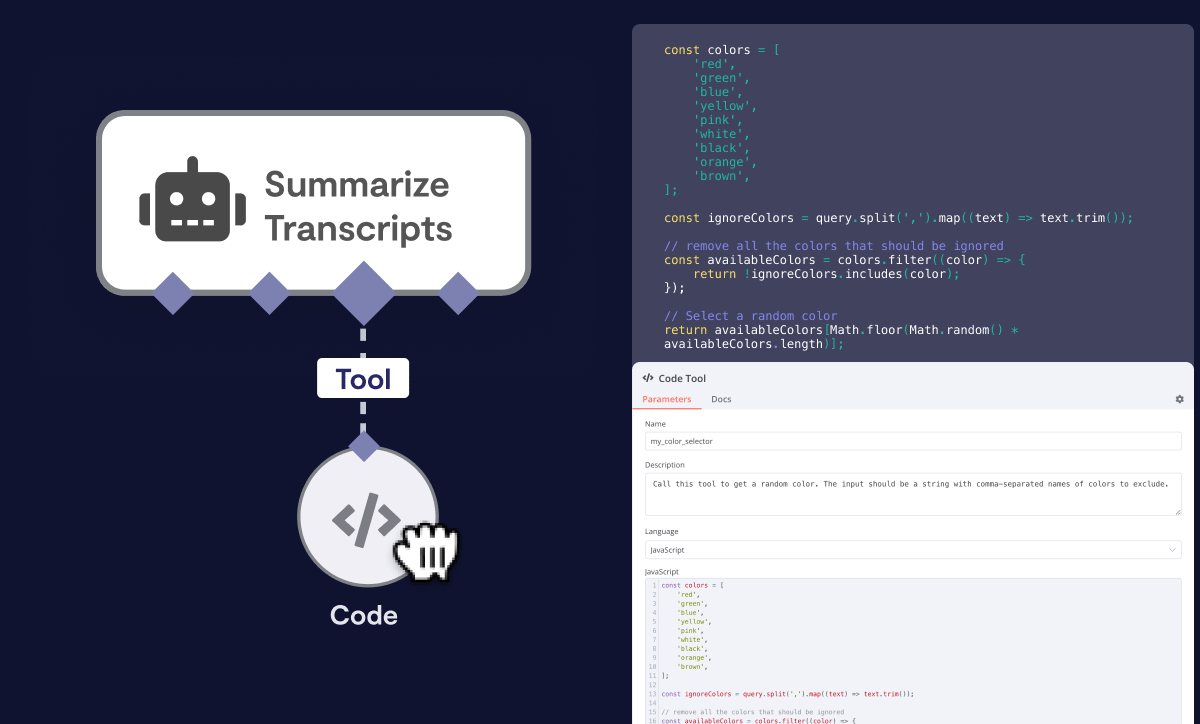
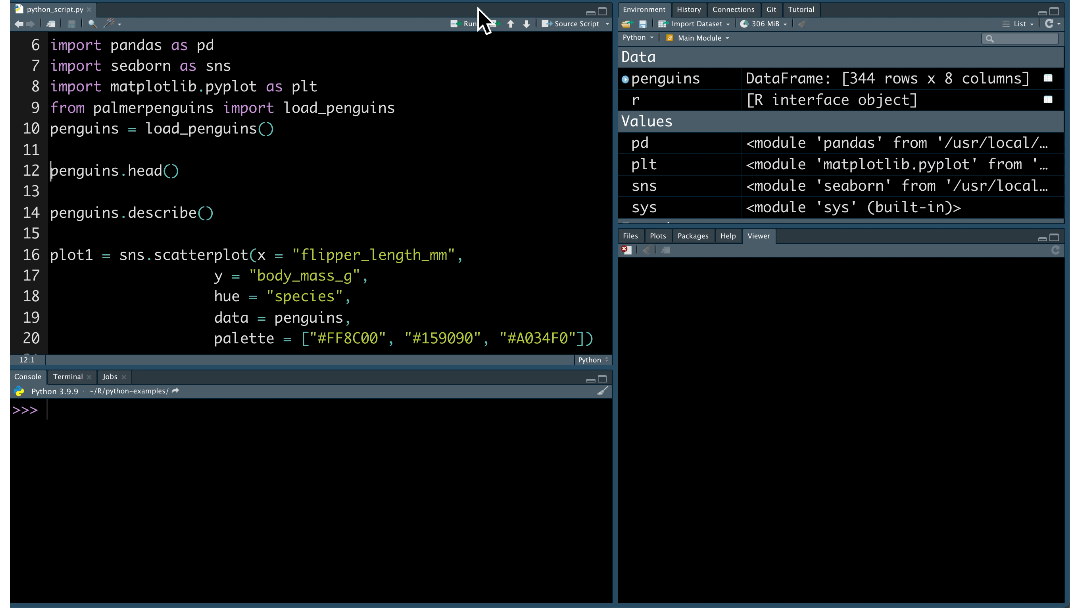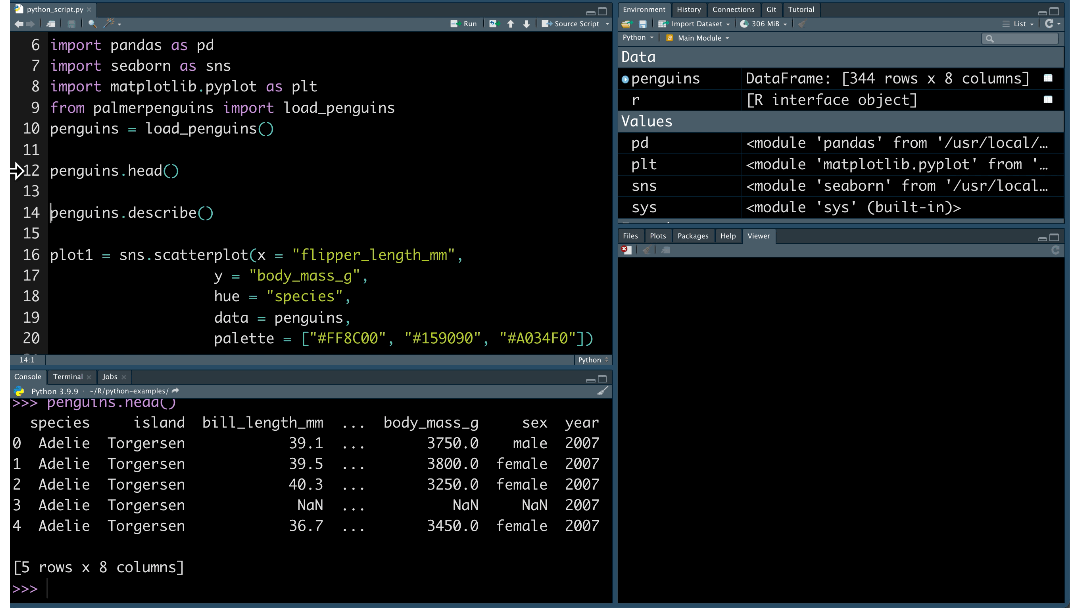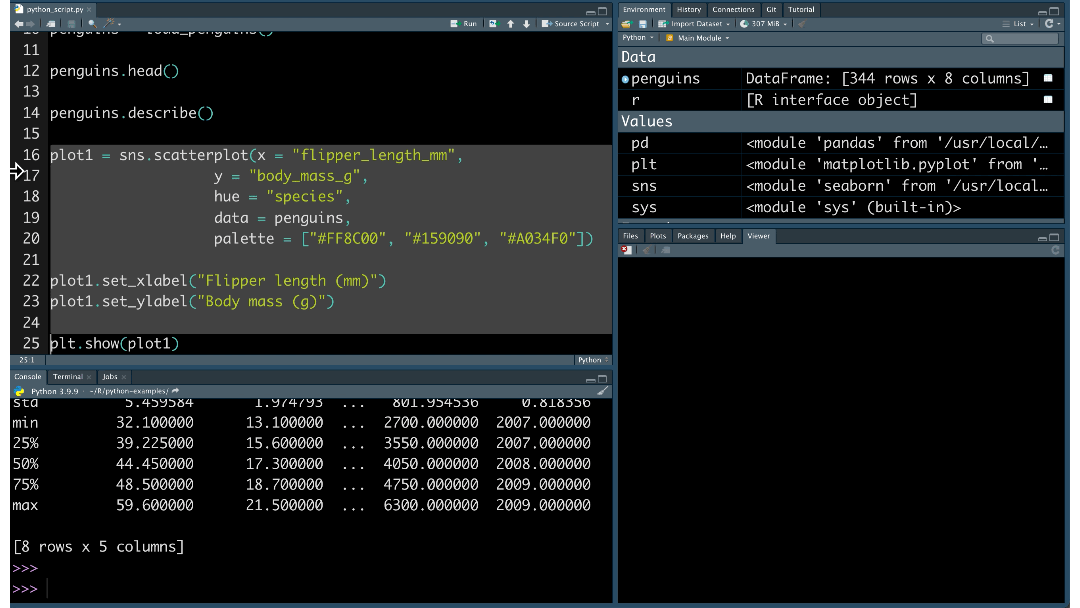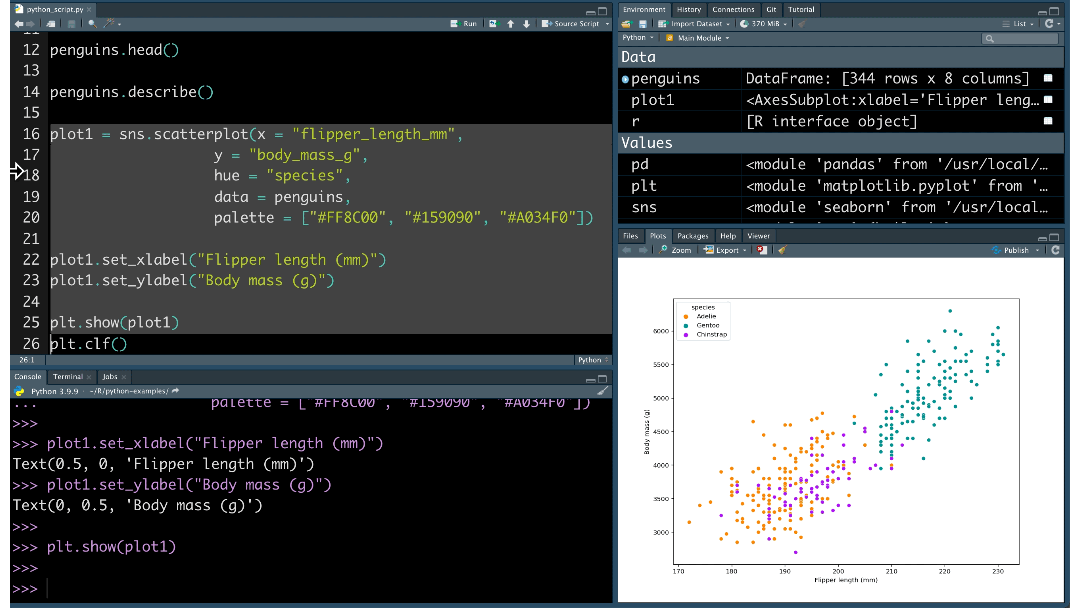
AI to custom data sources
mahliatov gives you peace of mind that attack traffic will be automatically blocked at the edge – without you having to increase bandwidth to pay for it. Unlimited protection against attacks of any size or duration